Here is a list of Technology Blogs ordered by Last Viewed, posted by members. A Blog is a journal you may enter about your life, thoughts, interesting experiences, or lessons you've learned. Post an opinion, impart words of wisdom, or talk about something interesting in your day. Update your blog on a regular basis, or just whenever you have something to say. Creating a blog is a good way to share something of yourself with others. Reading blogs is a good way to learn more about others. Click here to post a blog.

Google update!

Torrent Downloading Anonymity Lesson 2 Securing Yo
Seen blogs about downloading Torrents?
Okay cool yeah get it for free But Alarm.
How to Stay Anonymous While Torrenting?
HOW TO MAKE VPNS EVEN MORE SECURE
From being a niche product used by the few, in the past few years VPN services have hit the big time. These days more and more Internet users see running a privacy enhancing service as a requirement rather than just a luxury. Today we take a look at a few tips and tricks that can enhance the security of any VPN.
While simple to set up and use out of the box, it may comes as a surprise that the security of VPN anonymity services can be improved. Of course, when things run absolutely to plan there’s little to worry about, but there are occasions where there may be a hiccup or where an extra level of security is needed.
SECURING YOUR PRIVACY WHEN YOUR VPN FAILS
Ok, so you’ve purchased your VPN subscription, enabled the service, and you’re enjoying your new found levels of privacy. Then – disaster strikes. While you were away from your machine somehow and for some unknown reason your VPN disconnected and now snoopers have a clear view of your IP address.
To protect against the event of VPN failure/disconnection, disable any internet access that does not tunnel through your VPN service provider,” Andrew from PrivateInternetAccess “This can be achieved using specific Firewall rules (Ubuntu) or by changing TCP/IP routes.
But of course, not everyone wants to spend time with these manual configurations that could potentially cause problems if they’re not done properly.
the creators of two free pieces of software that do the job more easily.
VPNETMON
“VPNetMon continuously watches the IP addresses of your PC. If the IP address of your VPN is not detected anymore, VPNetMon closes specified programs instantly. The program reacts so quickly that a new connection through your real IP will not be established by these applications,”
VPNetMon (Windows) can be downloaded.
VPNCHECK
“VPNCheck helps you to feel safe if your VPN connection breaks, this is done by shutting down your main network connection or programs of your choice and showing a notification box,” Jonathan from Guavi.com “Basically it constantly looks for a change in your VPN network adapter. You can connect to either PPTP or L2TP with VPNCheck.”
VPNCheck (Windows/Linux) can be downloaded
STOP DNS LEAKS
When using a VPN service one might expect that all of the user’s traffic will go through the privacy network, but on rare occasions a phenomenon known as “DNS leakage” might occur. This means that rather than using the DNS servers provided by the VPN operator, it’s possible that the user’s default DNS servers will be used instead or otherwise become visible.
“A DNS leak may happen whenever a DNS query ‘bypasses’ the routing table and gateway pushed by the OpenVPN server. The trigger on Windows systems may be as simple as a slight delay in the answer from the VPN DNS, or the VPN DNS unable to resolve some name,” explains Paolo from AirVPN.
A tool for checking for leaks can be found at DNSLeakTest.com
If you don’t trust your VPN provider 100%, use two VPNs
This way you are tunneling your already encrypted connection through another tunnel.
PAY FOR YOUR VPN WITH UNTRACKABLE CURRENCY.
When anonymity is a factor, pay with an un-trackable currency
ONLY USE VPN PROVIDERS THAT TAKE YOUR PRIVACY SERIOUSLY
To be Continued post 1 of 2
grin
From an Old X
DARKSIDE RG AND THE PIRATEBAY HELLRAZOR
NOTE:PLEASE DO NOT ASK FOR BEST SITES TO OBTAIN TORRENTS
FIND THEM YOURSELVES YOU HAVE THE INTERNETgrin
AND I've Disabled Comments on this blog
 online today!
online today!
Microsoft is spying on me...
I'm online making a purchase and when I get to the cart to review, banners fly out to show the same items elsewhere at a lower cost.
Amazon and Walmart, but the savings were less than a dollar per item.
Since my purchase with this vendor has free shipping over $100, it makes no sense to break an order up to 3 vendors. Kinda like spending a dollar to save a dime. Triple billing, triple deliveries, triple order tracking.
Actually, the annoying part is Microsoft getting into my online purchasing. It may have been there in my previous computer (running Windows 10 with Edge) but I never noticed the banners before.
My computer is spying on me...
 online today!
online today!
Trouble opening blogs and mail,.....

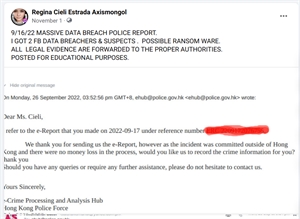
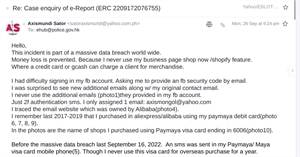
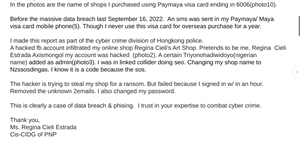
9/16/22 Cyber Attack Hunt
Got 2 data breachers last Seotember 16.
Reported to Hong Kong police.
They say they will take no action.
(Bluff! The report have been filed & recorded w/ a case number.
2nd email requests for recording & further information. Ok)
But they asks me nonstop.
For further information.
Gather evidence & come up with a positive suspect I.D.
Case is closed.
Now I can blog it
 online today!
online today!
Your Opinion
Would it not help to make it so much easier discerning between a scammer and a true potential match?
Hope this idea/suggestion does not cause too much discord among the scammers who have free reign.
Relax its weekend.
XXXXX is a free walkie-talkie app for smartphones, tablets, laptops and desktop computers. The app requires an Internet connection to work properly, whether it’s through Wi-Fi or a mobile data network. Unlike the standard calls you can make on the device of your choice, Zello connects you to fellow users and radio channels where large groups can talk regardless of distance.
Take note: I am not promoting any app or website.
More info for those genuinely interested:

Collecting huge amounts of data with WhatsApp
A few years ago WhatsApp made it possible to use WhatsApp in your web browser. That is good for user experience because composing a message on your keyboard is a lot easier than using those tiny touch screen buttons. It also makes copying/pasting and adding attachments easier. So much for the good news. The bad news is that it’s technically possible to use the WhatsApp Web interface to create a huge database of all possible WhatsApp users. There’s only a small group of users not affected: the users who have changed their privacy settings. Unfortunately, most users don’t change those privacy settings and WhatsApp doesn’t encourage it very much. These facts open up the possibility of collecting huge amounts of interesting data which i’m going to show you nowExplanation for normal users
Web WhatsApp connects to the WhatsApp servers by using your phone. In a nutshell the browser instructs the server to send back all the information for a certain phone number. Some of the information that’s being sent back include the following:
The profile picture
The status text or about text, the default texts is the famous ‘Hey there! I am using WhatsApp’
The online/offline status of the user
It turns out that the above information can be requested for every phone number. As said, it’s not necessary that the phone number has been added to your contact list. And because there is no such restriction, it’s possible to create a complete database of phone numbers, profile pictures, about texts and online/offline statuses. The database may be setup in such a way that complete timelines of phone numbers can be reconstructed. That answers questions like: when was the user with phone number xxx-xxxxxx online and offline?Almost all web sites that are being send to your browser, contain specific software that determines how the web site will function in your browser. Such software is written in Javascript. The software determines what happens when you click a button or move the mouse. But the software may also connect to a server to request certain kinds of information. The software in Web WhatsApp does that too. It sends a phone number to the WhatsApp server and in a few milliseconds it receives the information about that phone number. One of the nice things of that software is that everybody can take a look at the source code. That’s not all, you can also use the software by yourself by using certain parts of it stand alone. I’ve used that possibility to develop a script to request information from a huge range of phone numbers. That information contains the profile pictures, about texts and online/offline statuses. Everyone can create such a script.So, what can anyone do with al this information? First of all, again, imagine that anyone can create a database with the above information that contains all phone numbers for a certain country together with the profile pictures, about texts and online/offline statuses. This is in reach for a country like the Netherlands. The database kan be queried in such a way that it tells me when a phone number was online and it tells me what profile picture belongs to the phone number. After a few months it can tell me how often you have changed your profile picture and into what pictures. And how about facial recognition? Those techniques haven been improved over the last years. Imagine this, I take a walk and take a picture of some stranger. Now I feed the database that picture and in a few minutes it tells me which phone number belongs to the picture. Now that is quite scary, isn’t it?

Apple Helps Chinese Communists Suppress Protests
Sadly, the freedom protesters were not able to use AirDrop, a file-sharing feature on iPhones that allows users to share content in authoritarian states.
Apple removed the feature in their latest update in China and did not notify users.
Apple is working with the communists now.
Anti-government protests flared in several Chinese cities and on college campuses over the weekend. But the country’s most widespread show of public dissent in decades will have to manage without a crucial communication tool, because Apple restricted its use in China earlier this month.
AirDrop, the file-sharing feature on iPhones and other Apple devices, has helped protestors in many authoritarian countries evade censorship. That’s because AirDrop relies on direct connections between phones, forming a local network of devices that don’t need the internet to communicate. People can opt into receiving AirDrops from anyone else with an iPhone nearby.
That changed on Nov. 9, when Apple released a new version of its mobile operating system, iOS 16.1.1, to customers worldwide. Rather than listing new features, as it often does, the company simply said, “This update includes bug fixes and security updates and is recommended for all users.”
Hidden in the update was a change that only applies to iPhones sold in mainland China: AirDrop can only be set to receive messages from everyone for 10 minutes, before switching off. There’s no longer a way to keep the “everyone” setting on permanently on Chinese iPhones. The change, first noticed by Chinese readers of 9to5Mac, doesn’t apply anywhere else.
 online today!
online today!
drone rules...
A Blog is a journal you may enter about your life, your thoughts, interesting experiences, or lessons you have learned. It's your own page on Connecting Singles that you can update on a regular basis, or just whenever you have something to say. You can write about an opinion, impart words of wisdom, or talk about something interesting in your day. Creating a blog is a good way to share something of yourself with Connecting Singles members. Reading blogs is a good way to learn more about members you have met here. Please be sure to read the blog rules before posting.
Would YOU like to post a blog on Connecting Singles? Have you written blogs that you'd like to share with other members? Posting your blogs shows your skill and creativity and helps members get to know you better. Your blog will appear on the Connecting Singles Blogs page and also in a link on your profile page. Click here to post a blog »